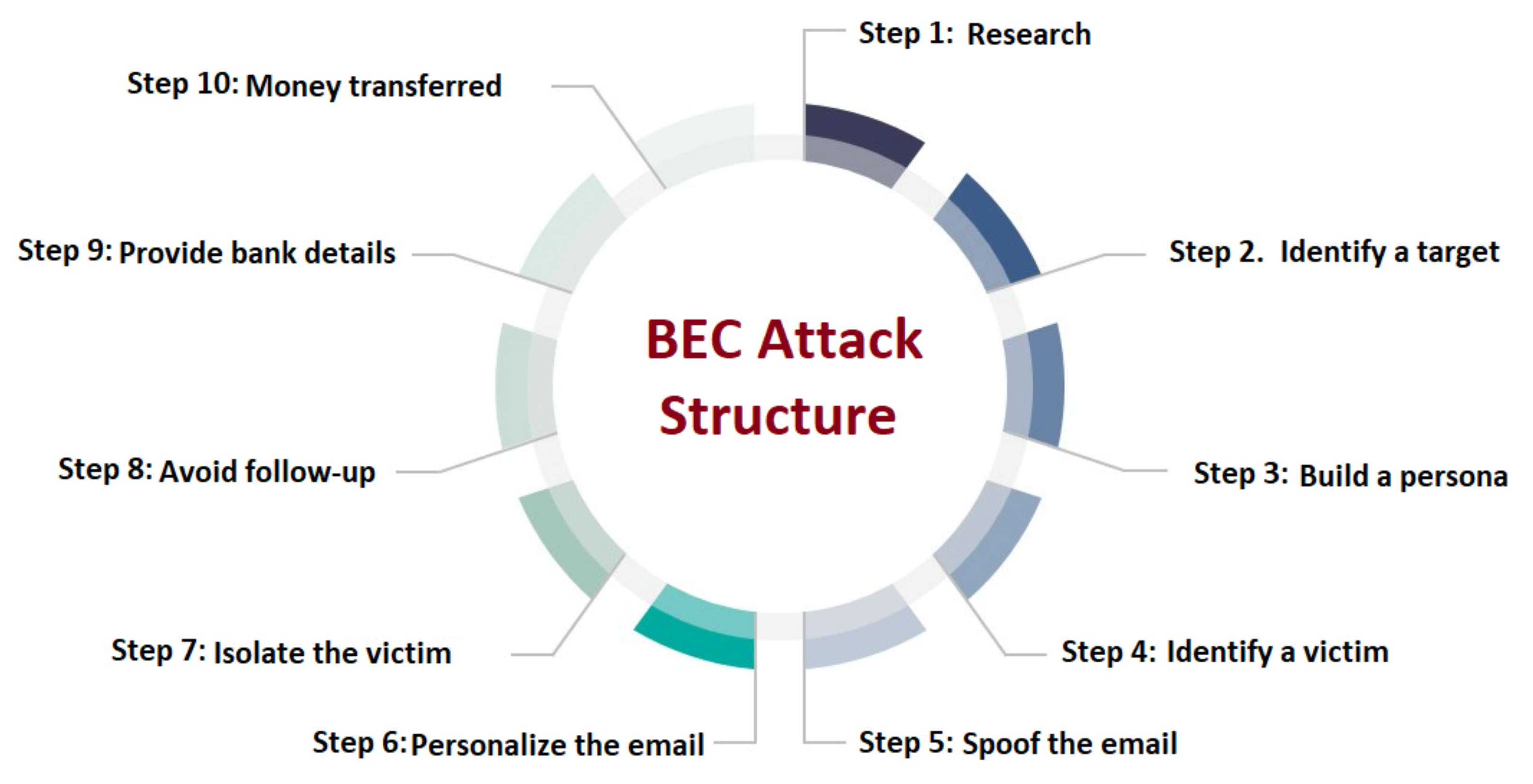
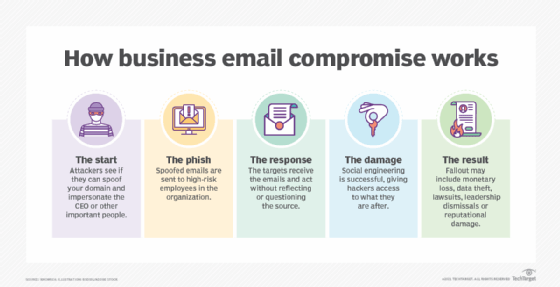
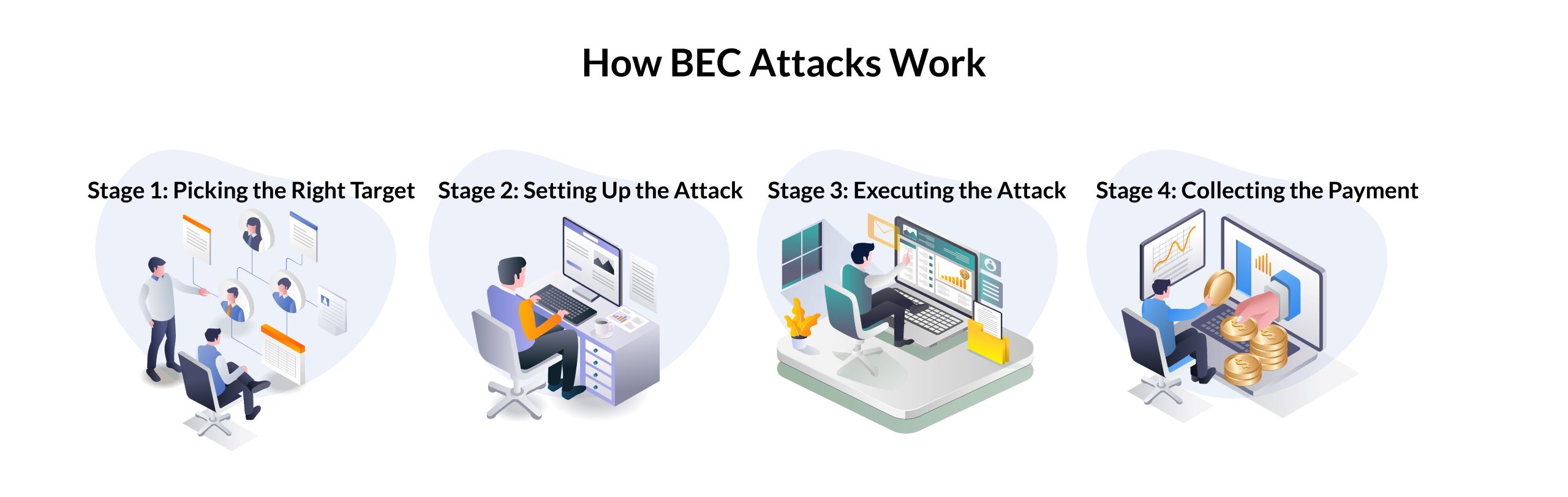
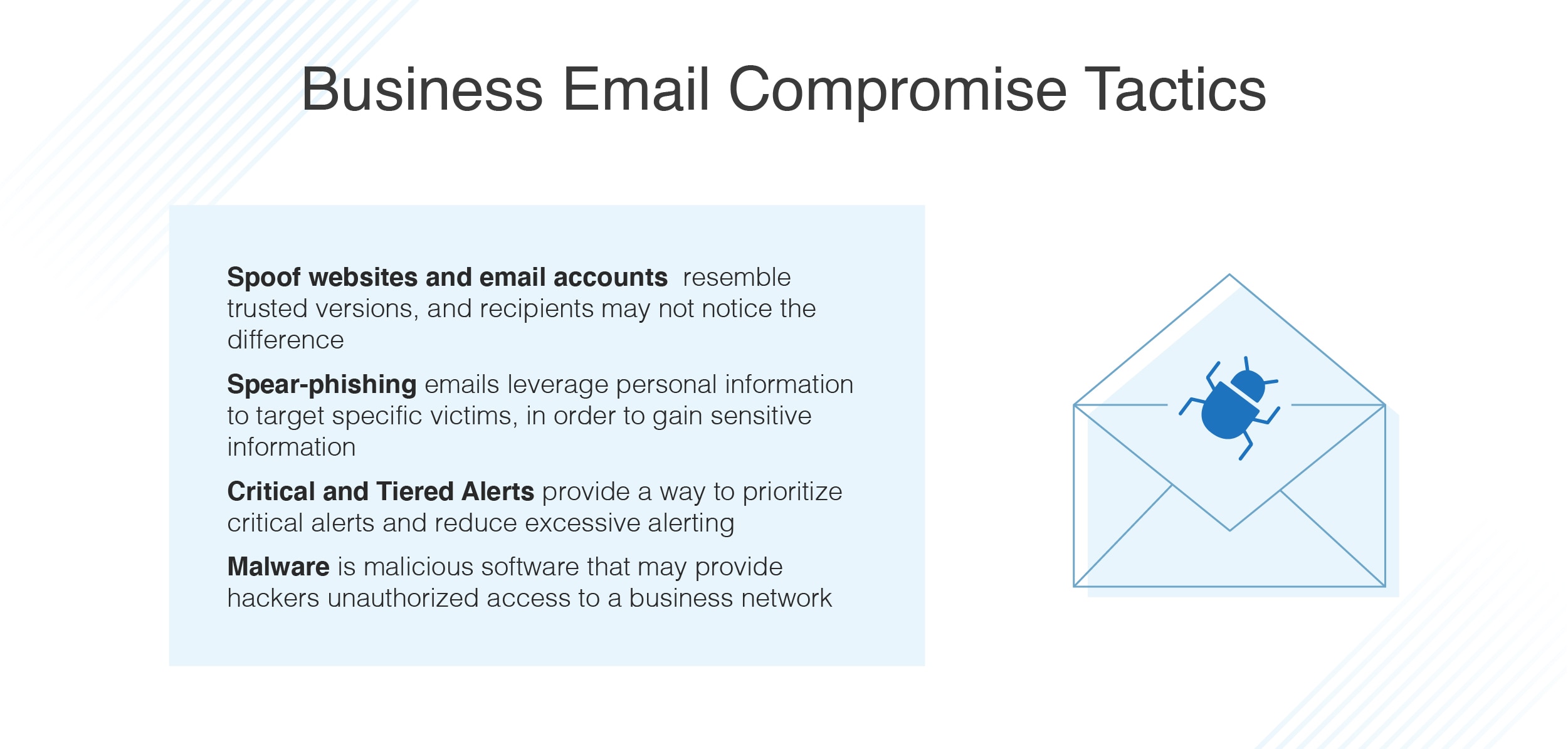
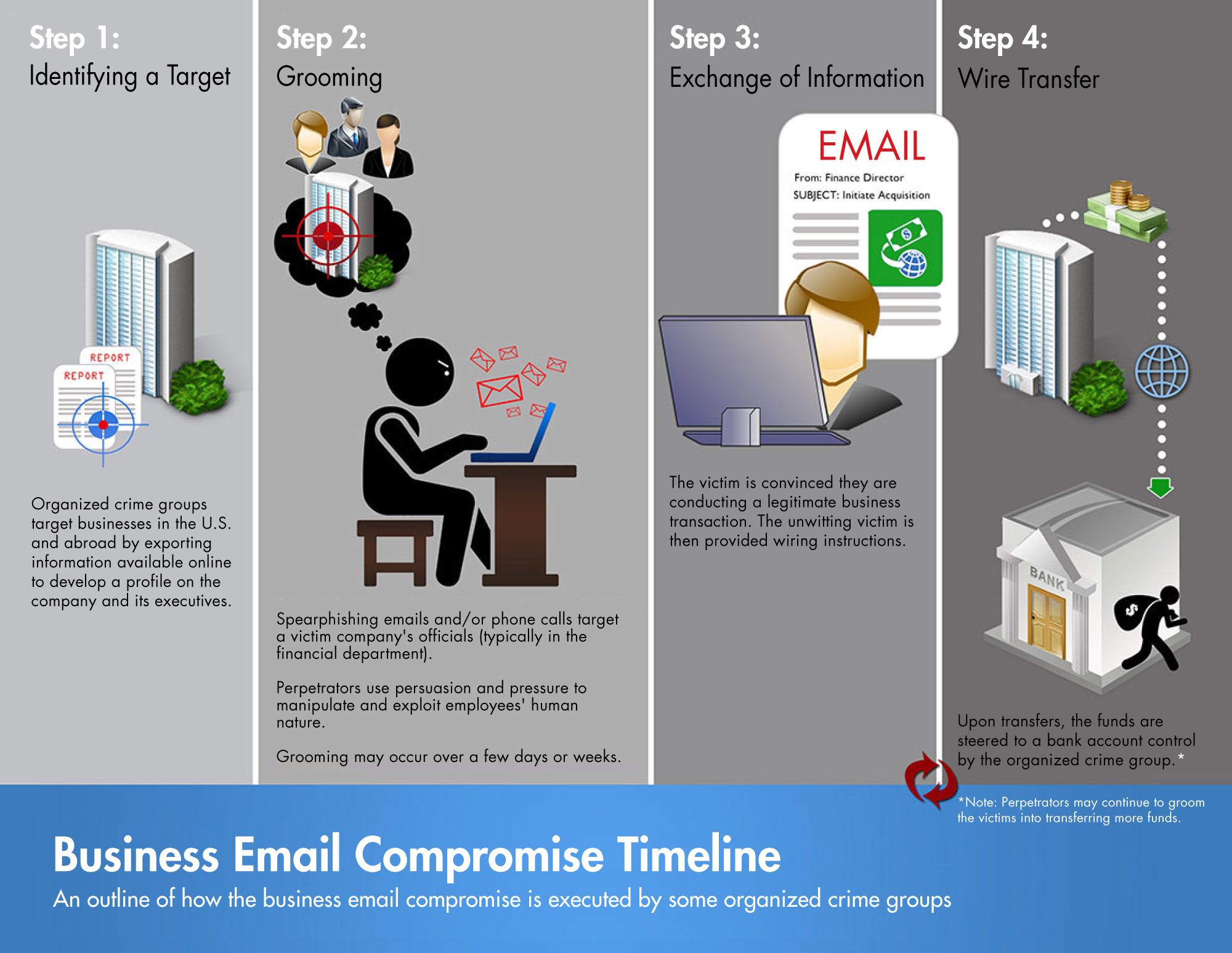
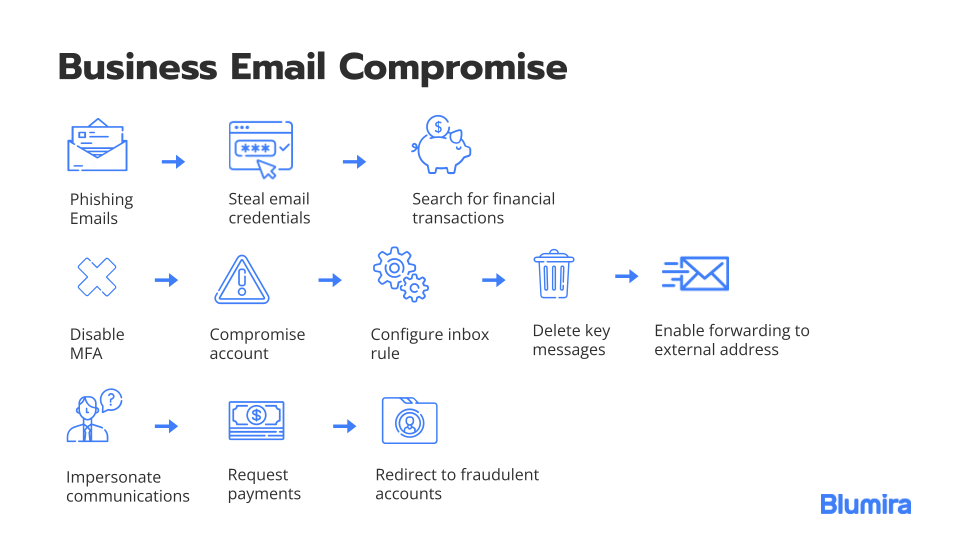
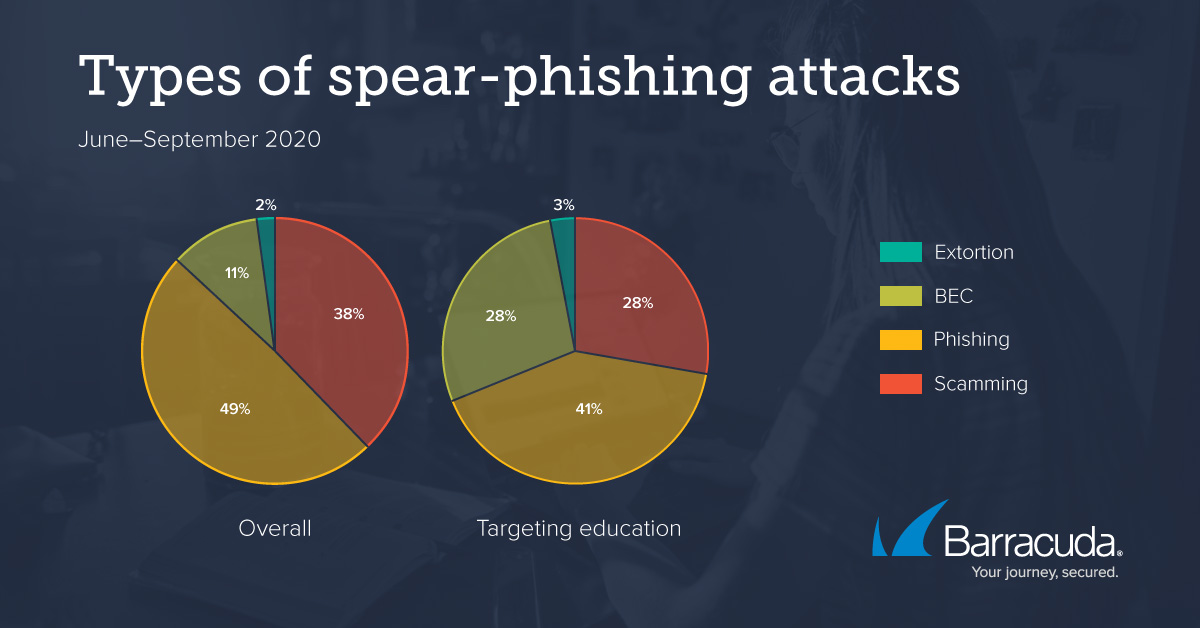
Billion-Dollar Scams: The Numbers Behind Business Email Compromise - Nachrichten zum Thema Sicherheit - Trend Micro DE

Business Process Compromise, Business Email Compromise, and Targeted Attacks: What's the Difference? - Security News

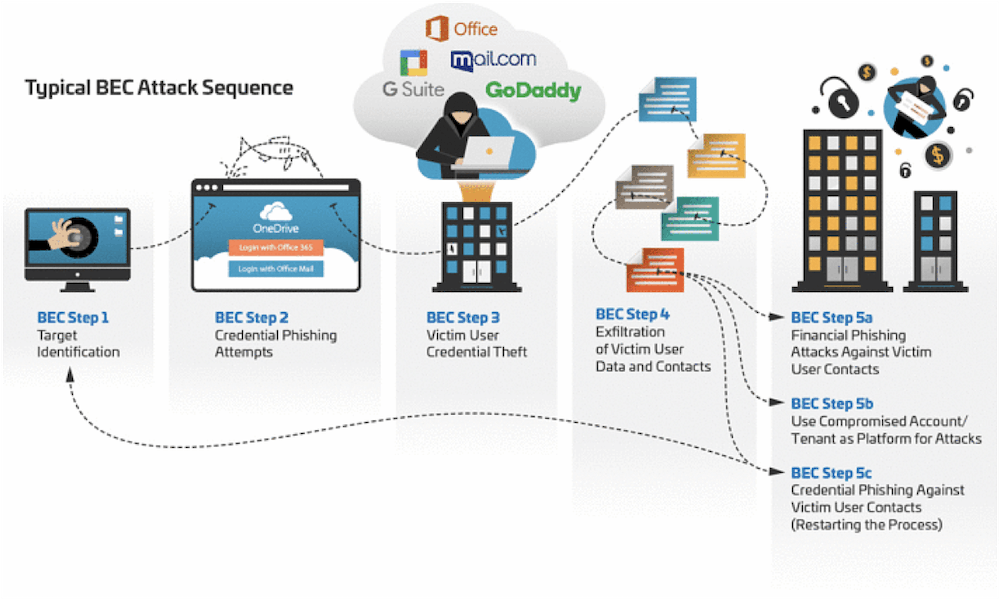
Behind the scenes of business email compromise: Using cross-domain threat data to disrupt a large BEC campaign | Microsoft Security Blog